Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...


Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit card...
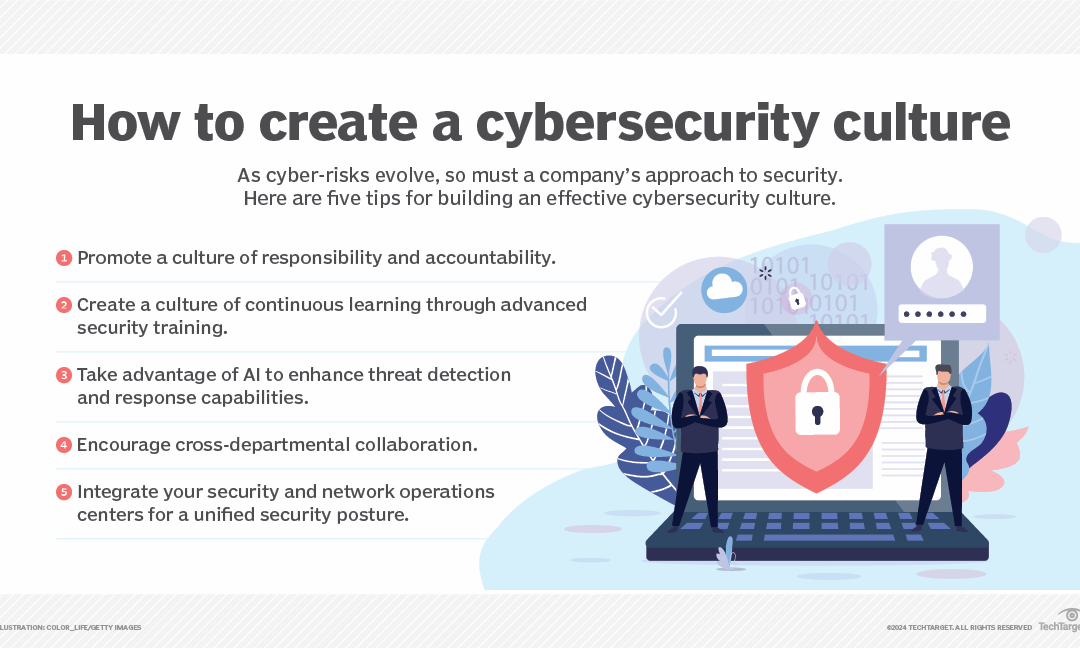
This in-depth cybersecurity planning guide provides information and advice to help organizations develop a successful strategy...

While home health agencies face distinct health IT challenges, collaboration and innovation are crucial for overcoming these...

The umbrella term malware is one of the greatest cybersecurity threats enterprises face. Learn about 12 common types of malware...
What is Cyber Security? In an era where our lives are intricately woven with digital threads, understanding cybersecurity is not just for IT professionals but for everyone. Cybersecurity refers to the practices, technologies, and processes designed to protect computers, networks, programs, and data from attack, damage, or unauthorized access. It’s the digital age’s shield, guarding the vast landscape of our interconnected world against cyber threats that seek to exploit vulnerabilities for nefarious purposes.
The journey of cybersecurity parallels the evolution of digital technology itself. From the rudimentary viruses of the early internet days to the sophisticated cyber-espionage campaigns of the 21st century, the complexity and scale of cyber threats have expanded dramatically. Today, cyber threats are not just about causing digital mischief but can have real-world implications, affecting everything from personal identity security to national security.
At its heart, cybersecurity revolves around the protection of digital information. The principles of confidentiality, integrity, and availability, often referred to as the CIA triad, form the cornerstone of cybersecurity efforts:
The realm of cybersecurity is vast, encompassing various domains to provide a holistic defence mechanism:
As technology evolves, so do cybersecurity measures. The incorporation of Artificial Intelligence (AI) and Machine Learning (ML) in cybersecurity tools is becoming more prevalent, providing advanced threat detection capabilities. The advent of blockchain technology offers new ways to secure transactions, and the proliferation of IoT devices has expanded the scope of cybersecurity to include the protection of connected devices.
The ramifications of a cybersecurity breach can be profound, affecting not just financial standings but also eroding trust and reputation. Thus, adopting a proactive stance toward cybersecurity is imperative. This entails keeping software up-to-date, conducting regular security assessments, and having an effective incident response strategy in place.
The responsibility of cybersecurity doesn’t rest solely on organizations; individuals also play a crucial role. Simple practices such as using strong passwords, being cautious about email attachments, and staying updated on the latest cyber threats can significantly mitigate the risk of cyberattacks.
As we delve deeper into the digital age, the essence of What is Cyber Security? becomes not just about protecting data. But safeguarding our very way of life. Cybersecurity is a dynamic field, a constant game of cat and mouse between defenders and cyber adversaries. Understanding what cybersecurity entails, and staying informed about emerging threats. And adopting a proactive approach to digital security is paramount in this ongoing battle. In the vast expanse of the digital realm. Cyber security stands as the beacon of safety. Ensuring that our digital voyages are secure and resilient against the turbulent waves of cyber threats.
Worried about being a target for phishing attacks? Protect your company today!
Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity....
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit...