
by witgdev | Aug 14, 2024 | Cybersecurity blog
The umbrella term malware is one of the greatest cybersecurity threats enterprises face. Learn about 12 common types of malware and how to prevent them. By Sharon Shea, Executive Editor and Isabella Harford, Published on TechTarget 26 Jun 2024 Malware is one...

by witgdev | Aug 13, 2024 | Uncategorized
Recent cyberattacks against OneBlood and McLaren Health Care shed light on the operational challenges that targeted organizations face By: Jill McKeon, Associate Editor Published: 09 Aug 2024 on TechTarget Healthcare cyberattacks often result in data breaches,...

by witgdev | Aug 12, 2024 | Cybersecurity blog
Originally Published on TechTarget.com by Sharon Shea, Executive Editor and Alexander S. Gillis, Technical Writer and Editor What is cybersecurity? Cybersecurity is the practice of protecting internet-connected systems such as hardware, software and data from cyber...
by witgdev | Aug 9, 2024 | Cybersecurity blog
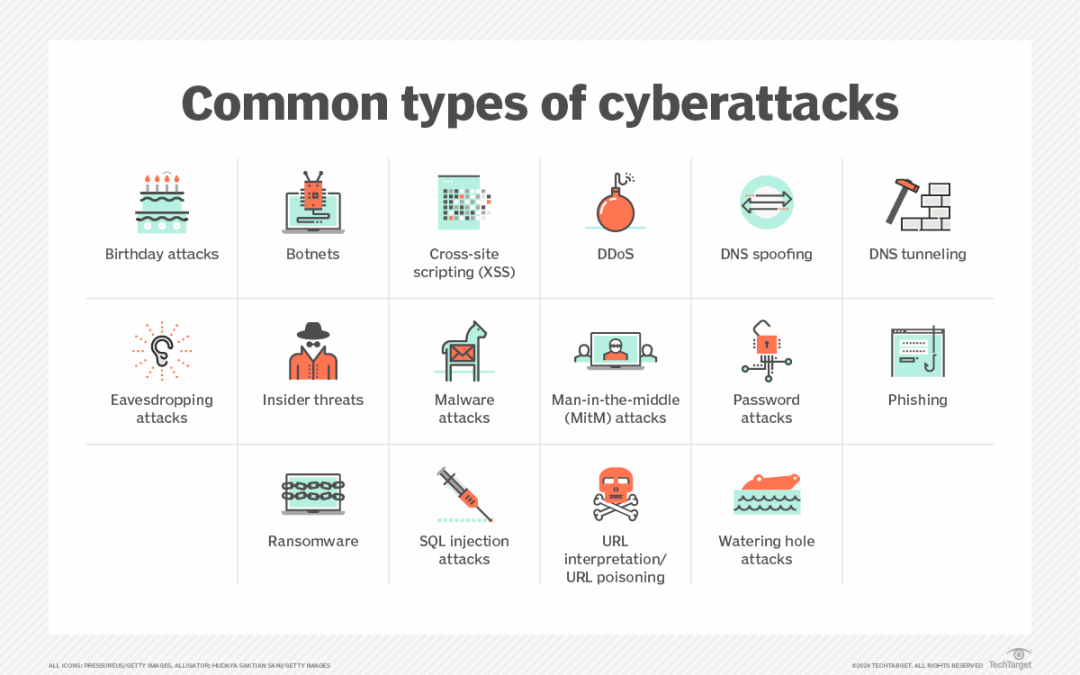
To stop cyberattacks, companies must understand how they’re being attacked. Here are the most damaging types of cyberattacks and what to do to prevent them. The original Article was published on techtarget.com on 05 Jul 2024 Today’s cybercriminals are not...

by Western IT | Aug 7, 2024 | Cybersecurity blog
In an era where data breaches and cyber threats are on the rise, cyber security for business is not just an option; it’s a necessity. Protecting your sensitive information from malicious attacks is crucial for maintaining your business’s integrity and trustworthiness....

by Rob Gallant | Jul 22, 2024 | Managed IT services blog
Contact Us Today Understanding IT Support What is an IT Support service? IT Support service: is a service that assists individuals and organizations in managing, maintaining, and troubleshooting their computer systems, networks, and other technology-related issues....

by Rob Gallant | Jul 16, 2024 | Communication, VoIP Service blog
Download PDF Voice over Internet Protocol (VoIP). Businesses are increasingly shifting from traditional Public-Switched Telephone Networks (PSTN) to modern Voice over Internet Protocol (VoIP) systems. This transition marks a significant change in how organizations...
by Rob Gallant | Jul 15, 2024 | Cybersecurity blog
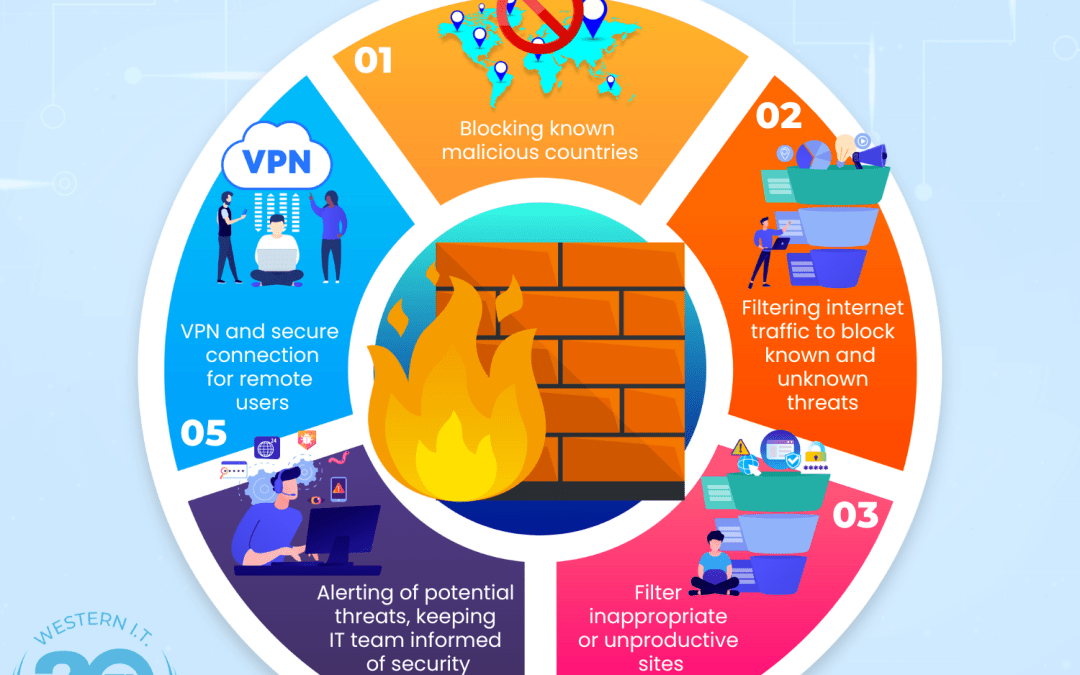
Download PDF Cybersecurity and Managed IT Services Understanding What is Cybersecurity? Cybersecurity refers to the practice of protecting systems, networks, and programs from digital attacks. These cyber-attacks are typically aimed at accessing, changing, or...

by Western IT | Jul 5, 2024 | Cybersecurity blog, Managed IT services blog
Western IT understands that Business IT Services and Business Cybersecurity require varied knowledge and skills. Local Perth Tech Support We have local Perth tech support staff trained in various products and with expertise in different areas to ensure a wide range of...

by Rob Gallant | Jul 2, 2024 | IT service
IT Support In today’s fast-paced digital world, businesses need robust IT support and comprehensive cybersecurity measures to stay ahead of the competition. If you’re looking for urgent IT support for business in Michigan or seeking top-notch cyber security solutions,...










