Why Your Business Needs Cybersecurity More Than Ever? In today's hyper-connected digital world, cybersecurity is no longer a...


Why Your Business Needs Cybersecurity More Than Ever? In today's hyper-connected digital world, cybersecurity is no longer a...

Worried about being a target for phishing attacks? Protect your company today!

Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit card...
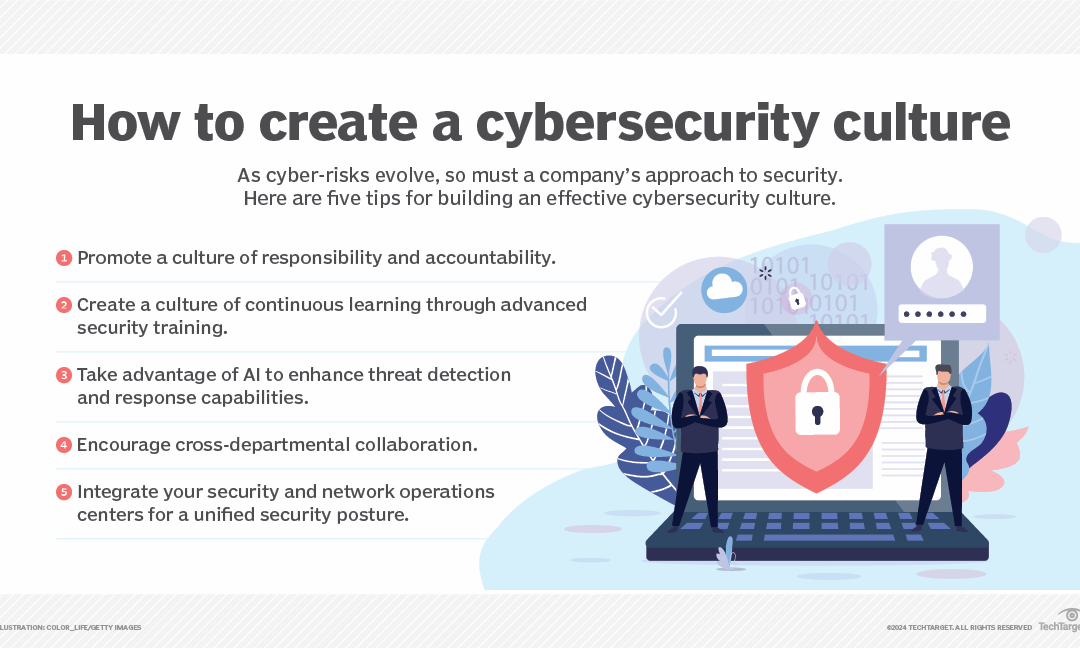
This in-depth cybersecurity planning guide provides information and advice to help organizations develop a successful strategy...

The Importance of Cybersecurity in Michigan. cybersecurity stands as a cornerstone of organizational resilience. Recent incidents underscore the critical need for robust cybersecurity measures, as cyber threats continue to evolve in sophistication and impact.
Cybersecurity encompasses the practices, technologies, and measures designed to protect digital systems, networks, and data from unauthorized access, cyber-attacks, and breaches. It involves a multidisciplinary approach that integrates aspects of technology, policy, and human behaviour to safeguard sensitive information and maintain the integrity of digital assets.
In today’s interconnected world, where organizations rely heavily on digital platforms for daily operations, cybersecurity plays a pivotal role in ensuring information confidentiality, availability, and integrity. It spans a wide range of disciplines, including network security, endpoint protection, data encryption, threat intelligence, and incident response, all aimed at fortifying defences against a diverse array of cyber threats.
Effective cybersecurity is essential for protecting businesses, governments, and individuals from the growing sophistication and frequency of cyber attacks. These attacks can range from ransomware and phishing schemes to more complex threats targeting critical infrastructure and sensitive data. The repercussions of a successful cyber attack can be severe, leading to financial losses, reputational damage, legal liabilities, and operational disruptions.
For businesses, cybersecurity is not merely a reactive measure but a proactive strategy that mitigates risks and enables sustainable growth. It enhances trust with customers and stakeholders by demonstrating a commitment to safeguarding sensitive information and ensuring business continuity. Moreover, compliance with regulatory standards and industry best practices in cybersecurity is increasingly becoming required, particularly in sectors handling sensitive data such as healthcare, finance, and government.
In addition to protecting against external threats, cybersecurity also addresses internal risks posed by inadvertent human errors, insider threats, and inadequate security protocols. Comprehensive cybersecurity frameworks include employee training and awareness programs to foster a culture of cybersecurity vigilance throughout the organization.
As digital transformation accelerates across industries, fueled by cloud computing, IoT (Internet of Things), and AI (Artificial Intelligence), the attack surface for cyber threats continues to expand. This evolution necessitates continuous adaptation and innovation in cybersecurity strategies to stay ahead of sophisticated cyber adversaries.
Government and international collaboration also play a crucial role in cybersecurity resilience, with initiatives aimed at enhancing cyber defence capabilities, sharing threat intelligence, and establishing global cybersecurity norms and standards.
A recent cyber attack targeting car dealerships in Metro Detroit has brought into sharp focus the devastating consequences of insufficient cybersecurity measures. The attack, which disrupted sales, financing, and payroll systems, illustrates how vulnerable businesses can be when faced with malicious cyber activities (CBS Detroit).
The cyber attack on car dealerships in Metro Detroit highlights the vulnerabilities inherent in today’s digital business landscape. In June 2024, several dealerships fell victim to a sophisticated cyber attack that crippled essential systems such as sales, financing, and payroll. This incident serves as a stark reminder of the severe consequences that businesses can face when cybersecurity measures are inadequate.
The attack on Metro Detroit car dealerships is not an isolated event but part of a broader trend of increasing cyber threats across various industries. Cyber attacks often exploit vulnerabilities in digital infrastructure, targeting gaps in security protocols and outdated software systems. For industries like automotive retail, heavily reliant on digital systems for daily operations, the disruption caused by such attacks can have significant financial implications and undermine customer trust.
In the aftermath of the cyber attack, affected dealerships resorted to manual processes such as using paper records for sales transactions, highlighting the immediate operational challenges businesses face during such incidents. Beyond these immediate disruptions, businesses may also encounter long-term repercussions such as loss of revenue, regulatory scrutiny, and damage to reputation. These consequences can profoundly impact the viability and competitiveness of affected businesses in the market.
The specific targeting of industries like automotive retail underscores a strategic approach by cybercriminals who exploit sectors perceived as less prepared or invested in cybersecurity defences. Industries such as automotive and healthcare, historically lagging in cybersecurity investments compared to sectors like finance and technology, are increasingly becoming prime targets for cyber attacks due to their critical reliance on interconnected digital systems.
This strategic targeting highlights the urgent need for businesses, including car dealerships in Michigan, to prioritize cybersecurity as a fundamental component of their operational strategy. By investing in robust cybersecurity frameworks that encompass proactive threat detection, continuous monitoring, and rapid incident response capabilities, businesses can better safeguard their digital assets and operations.
Government and regulatory bodies play a crucial role in enhancing cybersecurity resilience across industries. Initiatives such as the U.S. Senate Committee hearings on federal cybersecurity standards aim to harmonize and strengthen cybersecurity regulations. These efforts provide businesses with clearer guidelines and frameworks to bolster their defences against cyber threats, fostering a more secure digital environment for businesses and consumers alike.
Ultimately, the cyber attack on Metro Detroit car dealerships underscores the critical importance of ongoing investment in cybersecurity infrastructure and practices. By adopting a proactive approach to cybersecurity, businesses can mitigate risks, protect sensitive data, and ensure the resilience and continuity of their operations in an increasingly digital and interconnected world.
Across the globe, businesses of all sizes and across various sectors are increasingly vulnerable to sophisticated cyber threats. Industries perceived as ‘soft’ targets, such as healthcare and industrial control systems (ICS), face heightened risks due to historical underinvestment in cybersecurity infrastructure. Cyber attackers exploit vulnerabilities in these sectors’ digital systems, aiming to disrupt operations and exploit sensitive data for financial gain or malicious intent.
Healthcare systems and ICSs are particularly attractive targets for cyber attacks due to their critical role in public health and infrastructure management. Cyber attacks targeting healthcare organizations often aim to compromise patient records, disrupt medical services, or demand ransom payments through tactics like ransomware. Similarly, attacks on ICS can disrupt essential services such as power grids, water treatment plants, and transportation networks, posing significant risks to public safety and national security.
The consequences of cyber attacks extend beyond operational disruptions to encompass substantial financial and reputational risks for affected organizations. Financially, cyber attacks can result in direct financial losses from ransom payments, regulatory fines, legal fees, and the costs associated with restoring compromised systems. Moreover, the reputational damage stemming from a data breach or system compromise can erode customer trust, leading to potential loss of business, diminished investor confidence, and long-term brand damage.
In response to escalating cyber threats, governments worldwide are implementing stricter data protection regulations and cybersecurity standards. Organizations in sectors like healthcare and ICS must navigate complex regulatory landscapes, ensuring compliance with stringent data privacy laws and industry-specific cybersecurity frameworks. Failure to comply with regulatory requirements can result in severe penalties, further exacerbating the financial and operational impact of cyber attacks.
Western I.T. offers a robust suite of cybersecurity services designed to protect businesses from evolving cyber threats. Their offerings include WIT Protect, a comprehensive managed cybersecurity service that provides advanced antivirus and malware protection, regular system backups, and rapid recovery solutions. This service ensures continuous monitoring and defence against potential cyber threats, safeguarding your business’s digital assets.
Under the WIT 365 package, Western I.T. integrates antivirus and malware protection as a core component, employing a three-pronged defence strategy to shield against malware, ransomware, and malicious software. This proactive approach helps businesses in Michigan maintain uninterrupted operations, even in the face of breaches.
Western I.T.’s services also encompass WIT Assist Plus, offering 24/7 IT support and cyber attack remediation, ensuring compliance with regulatory standards and enhancing overall cybersecurity resilience. By investing in Western I.T.’s cybersecurity solutions, businesses can secure their digital infrastructure, protect sensitive data, and ensure operational continuity.
To mitigate the growing risks posed by global cyber threats, organizations must prioritize investments in robust cybersecurity measures. This includes deploying advanced threat detection technologies, implementing secure network architectures, and regularly updating software to patch known vulnerabilities. Proactive cybersecurity investments enable organizations to detect, prevent, and respond to cyber threats effectively, minimizing the likelihood and impact of successful attacks.
Collaboration within the cybersecurity community and information sharing among industry peers are essential strategies for enhancing collective defence against cyber threats. Participation in threat intelligence sharing platforms, industry-specific forums, and public-private partnerships facilitates the exchange of actionable threat intelligence and defensive strategies. By leveraging shared knowledge and insights, organizations can strengthen their cybersecurity posture and preemptively address emerging threats.
Human error remains a significant cybersecurity risk factor, emphasizing the importance of ongoing employee training and awareness programs. Educating employees about cybersecurity best practices, phishing awareness, and incident response protocols empowers them to recognize and mitigate potential threats proactively. By fostering a culture of cybersecurity awareness throughout the organization, businesses can enhance resilience against social engineering attacks and insider threats.
The increasing frequency and sophistication of cyber attacks underscore the critical need for organizations worldwide, including those in Michigan, to prioritize cybersecurity as a strategic imperative. By understanding global trends in cyber threats and their specific impact on sectors like healthcare and industrial control systems, businesses can enhance their defences against evolving cyber risks. Proactive measures such as enhanced cybersecurity investments, collaboration, and employee training not only mitigate financial and reputational risks but also safeguard critical infrastructure and ensure continuity of operations. Embracing cybersecurity as a shared responsibility enables organizations in Michigan and beyond to navigate complex cyber threats effectively and sustain long-term resilience in a rapidly evolving digital landscape.
In Michigan, as in many regions globally, the threat landscape for cybersecurity continues to evolve at a rapid pace. Organizations across various sectors, from automotive to healthcare and beyond, face increasing risks from cyber threats targeting sensitive data, operational systems, and customer trust. The state’s economic and industrial diversity makes it a prime target for cyber attackers looking to exploit vulnerabilities in digital infrastructure and capitalize on perceived weaknesses in cybersecurity defences.
Investment in robust cybersecurity infrastructure is critical to safeguarding Michigan’s businesses and institutions against the growing sophistication of cyber threats. This infrastructure encompasses advanced technologies such as intrusion detection systems, endpoint protection, secure network architectures, and encryption protocols. By implementing these technologies, organizations can fortify their defences, detect potential threats early, and mitigate the impact of cyber-attacks effectively.
Proactive risk management is essential for organizations aiming to stay ahead of emerging cyber threats. This approach involves continuous monitoring of IT systems for unusual activities, vulnerabilities, and potential security breaches. By leveraging threat intelligence and data analytics, organizations can identify and respond to threats in real time, minimizing the likelihood of successful cyber attacks and reducing operational disruptions.
Continuous monitoring of IT environments is fundamental to effective cybersecurity in Michigan. This practice allows organizations to detect and respond promptly to suspicious activities, unauthorized access attempts, and anomalies that could indicate a potential breach. Implementing automated monitoring tools and real-time alerts enables rapid incident response, ensuring that security incidents are addressed swiftly to mitigate their impact on business operations and data integrity.
Human factors remain a significant vulnerability in cybersecurity, underscoring the importance of comprehensive employee training and awareness programs. Educating employees about cybersecurity best practices, phishing awareness, data handling protocols, and incident response procedures equips them with the knowledge and skills to recognize, report, and mitigate potential cyber threats effectively. By fostering a culture of cybersecurity awareness, organizations empower their workforce to become proactive defenders against social engineering attacks and insider threats.
Collaboration within Michigan’s cybersecurity ecosystem is crucial for enhancing collective defence capabilities against cyber threats. Public-private partnerships, industry-specific forums, and participation in threat intelligence-sharing platforms enable organizations to share actionable insights, best practices, and defensive strategies. By pooling resources and expertise, businesses, educational institutions, and government agencies can strengthen their cybersecurity posture, preemptively identify emerging threats, and respond more effectively to cyber incidents.
Adhering to regulatory standards and cybersecurity frameworks is essential for organizations operating in Michigan. Compliance with regulations such as the Michigan Cyber Disruption Response Plan and industry-specific guidelines ensures that businesses meet legal obligations and maintain data privacy standards. By aligning cybersecurity practices with regulatory requirements, organizations not only mitigate legal risks but also enhance their overall cybersecurity resilience and trustworthiness among stakeholders.
In conclusion, the imperative for cybersecurity investment in Michigan cannot be overstated. As cyber threats evolve in complexity and frequency, organizations must adapt by prioritizing robust cybersecurity infrastructure, proactive risk management strategies, and collaborative initiatives. By investing in advanced technologies, continuous monitoring, employee training, and compliance with regulatory standards, businesses and institutions across Michigan can strengthen their defences against cyber threats, safeguard sensitive information, and ensure the resilience of Michigan’s digital economy. Embracing cybersecurity as a strategic priority enables organizations to navigate the evolving threat landscape effectively, protect critical assets, and uphold trust in an interconnected world.
Stay Safer, One Email at a Time: Introducing Our New AI-Powered Email Scanner In today's rapidly evolving digital...
Why Your Business Needs Cybersecurity More Than Ever? In today's hyper-connected digital world, cybersecurity is no...
Worried about being a target for phishing attacks? Protect your company today!