Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...


Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit card...
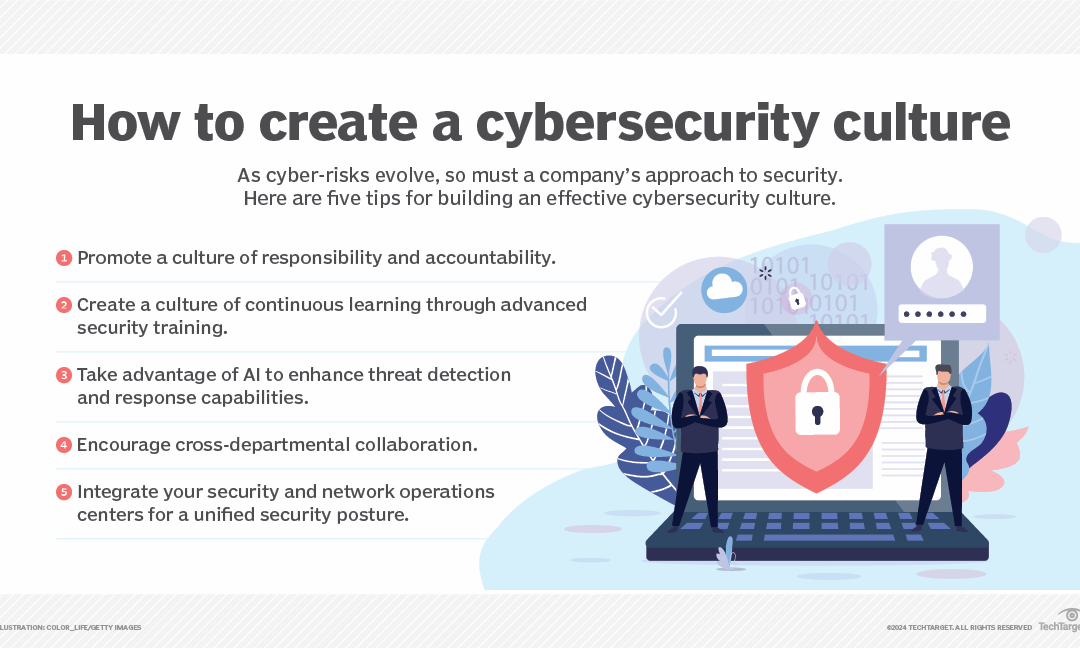
This in-depth cybersecurity planning guide provides information and advice to help organizations develop a successful strategy...

While home health agencies face distinct health IT challenges, collaboration and innovation are crucial for overcoming these...

Understanding Managed IT Services What Are Managed IT Services? Managed IT Services For business are the comprehensive...
ITSM vs. Managed IT Services. In the realm of information technology, terms like IT Service Management (ITSM) and Managed IT Services often get tossed around, sometimes interchangeably, creating confusion. Both play crucial roles in the modern business landscape, but they differ significantly in scope, approach, and execution. This blog aims to demystify these two concepts, highlighting their unique characteristics, applications, and how they complement each other in enhancing business operations.
ITSM is a strategic approach to designing, delivering, managing, and improving the way information technology (IT) is used within an organization. The focus is on ensuring IT services align with business needs and objectives, enhancing overall efficiency and productivity. ITSM encompasses a broad range of processes and frameworks, with ITIL (Information Technology Infrastructure Library) being one of the most prominent, providing a set of best practices for ITSM.
Key Characteristics of ITSM:
Managed IT Services, on the other hand, involve outsourcing specific IT operations and tasks to a third-party provider, known as a Managed Service Provider (MSP). This model allows businesses to offload the complexities of managing certain IT functions. Such as network management, data backup, cybersecurity, and helpdesk services, to experts in the field.
Key Characteristics of Managed IT Services:
While ITSM and Managed IT Services both aim to optimize IT functions within organizations, their approaches and scopes differ:
Despite their differences, ITSM and Managed IT Services are not mutually exclusive and can complement each other effectively within an organization. For instance, a company might adopt ITSM principles to streamline its IT services while also partnering with an MSP to manage specific functions like cybersecurity or cloud services. This hybrid approach leverages the strategic framework of ITSM and the operational efficiency of Managed IT Services. Providing comprehensive IT support that aligns with business objectives.
ITSM vs. Managed IT Services. Understanding the distinctions between ITSM and Managed IT Services is crucial for businesses looking to optimize their IT operations. ITSM offers a strategic framework focused on aligning IT services with business needs, emphasizing process efficiency and continuous improvement. Managed IT Services, meanwhile, provide operational support for specific IT functions, offering scalability, flexibility, and predictable costing through outsourcing. Together, they offer a robust solution for businesses aiming to enhance their IT capabilities while staying focused on their core missions. In navigating the complexities of modern IT. Recognizing the unique contributions and synergies of ITSM and Managed IT Services can lead to more informed decision-making and a more cohesive IT strategy.
Worried about being a target for phishing attacks? Protect your company today!
Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity....
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit...