Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...


Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit card...
This in-depth cybersecurity planning guide provides information and advice to help organizations develop a successful strategy...

While home health agencies face distinct health IT challenges, collaboration and innovation are crucial for overcoming these...

The umbrella term malware is one of the greatest cybersecurity threats enterprises face. Learn about 12 common types of malware...
Cybersecurity refers to the practice of protecting systems, networks, and programs from digital attacks. These cyber-attacks are typically aimed at accessing, changing, or destroying sensitive information, extorting money from users, or interrupting normal business processes. Implementing effective cybersecurity measures is particularly challenging today because there are more devices than people, and attackers are becoming more innovative.
The prevalence of cyber threats has skyrocketed, presenting unprecedented challenges for businesses of all sizes. Cyber attacks, ranging from ransomware to sophisticated phishing schemes, are not just occasional disturbances but persistent threats that can severely disrupt business operations, compromise sensitive data, and tarnish reputations. The increasing frequency and complexity of these cyber threats underscore the critical importance of robust cybersecurity measures in protecting business assets.
The modern business landscape is heavily reliant on digital infrastructure, making companies vulnerable to a variety of cyber threats. According to recent studies, cybercrime is expected to inflict damages totalling $6 trillion globally by 2021, projected to grow in the coming years. These alarming statistics highlight a pressing need for businesses to fortify their defences against cybercriminals. Cybersecurity is no longer a luxury but a necessity for survival in a digitally connected world. A single breach can lead to catastrophic financial losses, legal repercussions, and a loss of customer trust that can take years to rebuild.
This reality places immense pressure on businesses to prioritize cybersecurity. However, ensuring comprehensive protection goes beyond merely installing antivirus software or setting up firewalls. It requires a multifaceted approach that includes robust IT support, comprehensive cybersecurity strategies, and managed IT services. Robust IT support ensures that technical issues are promptly addressed, minimizing downtime and maintaining operational efficiency. IT support teams also play a pivotal role in implementing and maintaining security protocols safeguarding digital assets.
Comprehensive cybersecurity measures are essential in creating a resilient defence against cyber threats. This includes protecting the network and securing endpoints, encrypting sensitive data, and ensuring regular backups. Cybersecurity training for employees is equally crucial, as human error remains one of the leading causes of security breaches. Educating staff about the latest threats and safe online practices can significantly reduce the risk of successful attacks.
Managed IT services offer a proactive approach to cybersecurity, providing continuous monitoring and maintenance of IT infrastructure. These services ensure that security measures are always up to date, vulnerabilities are promptly addressed, and any unusual activity is quickly identified and mitigated. By outsourcing IT management, businesses can leverage the expertise of cybersecurity professionals who stay abreast of the latest threats and technologies, offering a level of protection that might be challenging to achieve in-house.
The scope of cybersecurity encompasses several critical components, each serving a specific purpose in the overall defence strategy:
The digital landscape is rife with various cyber threats, each posing unique risks to businesses and individuals. Understanding these threats is the first step in building a robust defence strategy.
Cyber threats pose significant financial and reputational risks to businesses. Financially, the direct costs of a cyber attack can be staggering. These costs include immediate expenses such as IT remediation, legal fees, regulatory fines, and compensation for affected customers. Additionally, there are long-term financial impacts, such as increased insurance premiums and investment in improved security measures. According to a report by IBM, the average cost of a data breach in 2020 was $3.86 million, a sum that can be devastating for small to mid-sized enterprises.
Beyond direct financial losses, businesses also suffer from operational disruptions. Cyber attacks can cause significant downtime, leading to lost sales and reduced productivity. For instance, ransomware attacks can lock users out of critical systems, halting business operations until the ransom is paid or systems are restored from backups. The longer the downtime, the greater the financial impact.
Reputational damage is another severe consequence of cyber attacks. Trust is a crucial asset for any business, and a security breach can erode that trust rapidly. Customers and partners expect their data to be protected, and a breach can lead to a loss of confidence in the company’s ability to safeguard sensitive information. This loss of trust can result in customer attrition, reduced sales, and difficulties in acquiring new customers. Moreover, the negative publicity associated with a cyber attack can tarnish a company’s brand image, making it challenging to rebuild its reputation.
Real-life examples of businesses affected by cyber attacks illustrate the profound impact these incidents can have:
IT helpdesk services play a crucial role in maintaining the cybersecurity posture of an organization. These services serve as the first line of defence against technical issues and cyber threats. An effective IT helpdesk can quickly address and resolve technical problems that could potentially be exploited by cyber attackers. For instance, outdated software or misconfigured systems can be identified and corrected by helpdesk personnel, reducing the risk of vulnerabilities.
Moreover, IT helpdesk services support cybersecurity efforts by assisting users with security-related queries and issues. This includes helping employees with password resets, guiding them on secure practices, and responding to suspected phishing attempts or malware infections. The helpdesk acts as a central point for reporting and managing security incidents, ensuring that any threats are promptly escalated to the appropriate cybersecurity teams for further action.
A well-trained helpdesk team can also provide proactive support by educating users about common cyber threats and safe computing practices. By fostering a security-conscious culture, the helpdesk helps minimize human errors, which are often the weakest link in the cybersecurity chain.
Both remote and onsite IT support are integral to maintaining robust cybersecurity, but they offer different benefits and face distinct challenges.
Remote support allows IT professionals to manage and resolve issues from a distance, which is particularly beneficial for businesses with multiple locations or remote workers. Remote support can provide rapid response times, as technicians can access systems quickly without the need for travel. This immediacy is crucial in addressing security incidents promptly and minimizing potential damage. Remote support is also cost-effective, reducing the need for onsite visits and associated travel expenses.
However, remote support has its limitations. Certain issues, such as hardware failures or network infrastructure problems, may require physical presence to resolve. Additionally, remote access itself must be secure to prevent unauthorized access. Properly secured remote support tools and protocols are essential to avoid creating new vulnerabilities.
Onsite support provides the advantage of physical presence, which is sometimes necessary for comprehensive security assessments, hardware maintenance, and infrastructure upgrades. Technicians can perform hands-on troubleshooting and repairs, ensuring that physical and network security measures are properly implemented and maintained. Onsite support is particularly valuable for addressing complex issues that require direct interaction with systems and users.
The primary drawback of onsite support is the time and cost associated with travel, especially for businesses with dispersed locations. However, the benefits of having IT personnel physically present to handle intricate problems and interact directly with users often outweigh these challenges.
Firewalls and network security are foundational components of a robust cybersecurity strategy. A firewall acts as a barrier between an internal network and external threats, monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. Firewalls can prevent unauthorized access, block malicious traffic, and detect suspicious activities.
Network security encompasses a broader range of practices and technologies designed to protect the integrity, confidentiality, and availability of data as it is transmitted and received across networks. This includes intrusion detection systems (IDS) and intrusion prevention systems (IPS) that monitor network traffic for signs of malicious activity and take action to prevent breaches. Network segmentation, which involves dividing a network into smaller, isolated segments, can also enhance security by containing potential breaches and limiting their spread.
Antivirus software is essential for protecting computers and networks from a wide range of malware, including viruses, worms, Trojan horses, ransomware, spyware, and adware. Antivirus solutions detect, quarantine, and remove malicious software, preventing it from causing harm to systems and data.
For businesses, having robust antivirus protection is critical due to the potential impact of malware on operations and data integrity. Business antivirus solutions often include additional features such as real-time scanning, automatic updates, and centralized management, allowing IT teams to monitor and control security across all devices. Regular updates are crucial to ensure that the antivirus software can recognize and defend against the latest threats.
Employee cybersecurity training is a vital component of an organization’s overall security strategy. Despite advanced technical defences, human error remains one of the most significant vulnerabilities. Social engineering attacks, such as phishing, rely on manipulating individuals to gain unauthorized access to systems and data.
Effective cybersecurity training programs educate employees about common threats, safe computing practices, and the importance of following security protocols. Training should cover how to recognize phishing emails, create strong passwords, and securely handle sensitive information. Regular training sessions and simulated phishing exercises can reinforce good habits and help employees stay vigilant against evolving threats.
Training should also emphasize the importance of reporting suspicious activities to the IT helpdesk or security team. Encouraging a culture of openness and vigilance can significantly enhance an organization’s ability to detect and respond to threats quickly.
Managed IT services refer to the practice of outsourcing a range of IT tasks and responsibilities to a third-party provider. These services are designed to support and manage an organization’s IT infrastructure, improve operational efficiencies, and reduce costs. Managed IT services encompass a broad spectrum of solutions that ensure the smooth and secure operation of a business’s IT environment.
The benefits of managed IT services for businesses are manifold. Firstly, they provide access to a team of experts who can handle various IT needs, from network security to software updates, allowing businesses to focus on their core activities. Managed IT services also offer predictable costs through a subscription-based model, making budgeting easier. Additionally, these services ensure that businesses stay up-to-date with the latest technologies and best practices without the need for continuous in-house training and development.
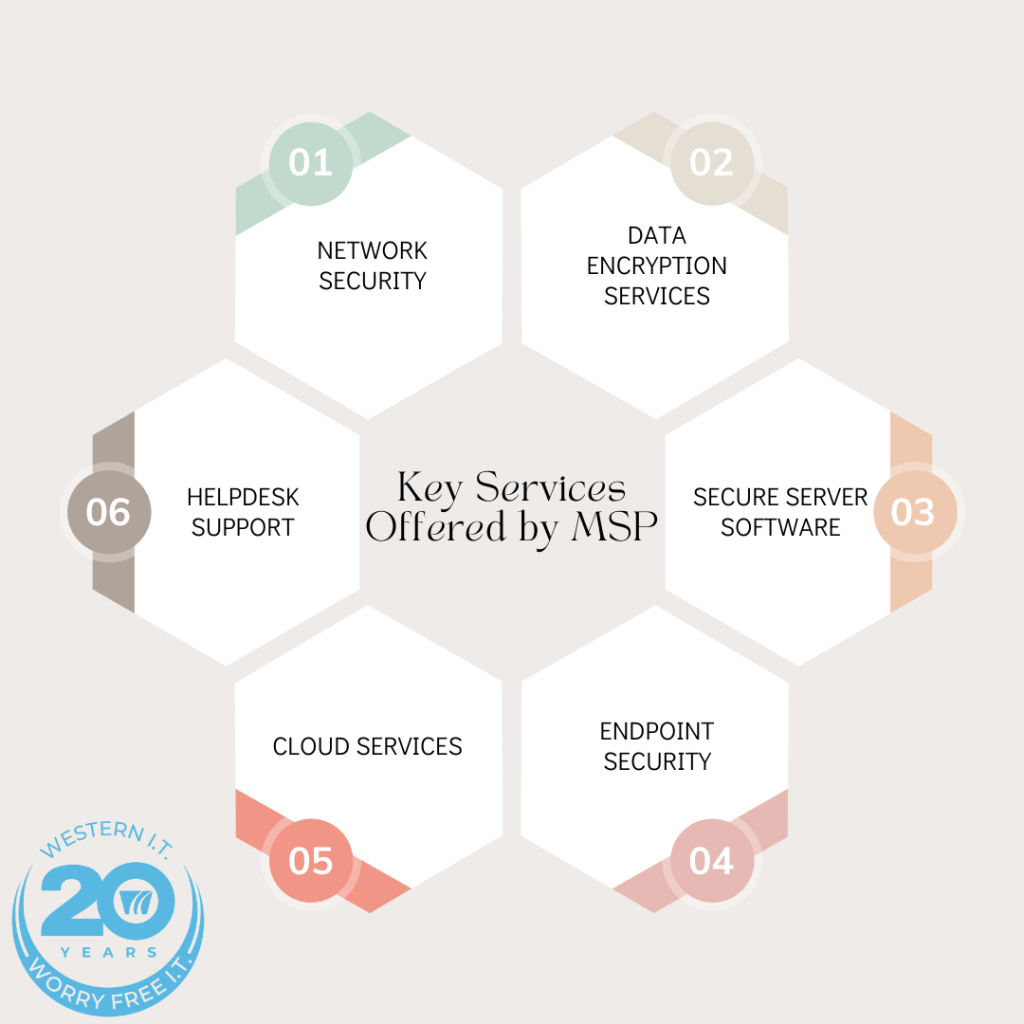
Managed IT service providers offer a comprehensive range of services to meet the diverse needs of businesses. Key services include:
Disaster recovery plans are essential for ensuring business continuity in the event of a catastrophic event such as a cyber attack, natural disaster, or system failure. These plans outline procedures for restoring IT systems and data to minimize downtime and loss. Without a robust disaster recovery plan, businesses risk severe operational disruptions, financial losses, and damage to their reputation.
A disaster recovery plan typically includes steps for data backup, system restoration, and communication with stakeholders. It ensures that critical business functions can resume quickly and that data integrity is maintained. By preparing for potential disasters, businesses can reduce the impact of unforeseen events and recover more swiftly.
Cloud backup and onsite backup solutions are two primary methods for safeguarding business data.
Cloud Backup: Cloud backup involves storing data on remote servers managed by a third-party provider. This method offers several advantages, including scalability, automatic backups, and offsite storage, which protects data from local disasters. Cloud backups can be accessed from anywhere, providing flexibility and ensuring that data recovery is possible even if the primary site is compromised.
Onsite Backup: Onsite backup involves storing data on physical devices located within the business premises. This method allows for faster data recovery times since the data is stored locally. However, onsite backups are vulnerable to physical damage, theft, and local disasters.
Both methods have their merits, and many businesses opt for a hybrid approach that combines the benefits of both. This strategy ensures data redundancy and enhances recovery capabilities.
Server backup solutions are critical components of disaster recovery plans. They ensure that all data stored on servers is regularly backed up and can be restored in the event of data loss or system failure. Effective server backup solutions involve both full and incremental backups, allowing for efficient storage management and quick restoration times.
Server backups can be performed using various methods, including disk-based, tape-based, and cloud-based solutions. Regular testing of backup and recovery procedures is essential to ensure that the system functions correctly and data can be restored without issues.
Proper network and infrastructure setup are fundamental to the efficient operation of IT systems. Network switch installation and structured cabling installation are key elements of this setup.
Network Switch Installation: Network switches are devices that connect multiple devices on a local area network (LAN), directing data to its destination. Proper installation of network switches ensures that data traffic flows efficiently, reducing latency and improving network performance.
Structured Cabling Installation: Structured cabling involves the design and installation of a standardized cabling system that supports various hardware uses and is suitable for both current and future needs. This approach ensures reliable and scalable network infrastructure, reducing the risk of downtime and simplifying maintenance and upgrades.
CAT6 Installation: CAT6 cables are a type of twisted pair cable designed for Ethernet and other network physical layers. They support high-speed data transfer and are essential for modern business networks. CAT6 installation ensures that the network can handle high bandwidth demands, reducing lag and improving overall network performance.
Public WiFi Solutions: Public WiFi solutions provide internet access to customers, visitors, and employees in public or shared spaces. Implementing secure public WiFi solutions is crucial to protect the network from unauthorized access and cyber threats. These solutions should include encryption, user authentication, and regular monitoring to ensure security and reliability.
In conclusion, managed IT services offer comprehensive protection for businesses by providing a range of essential services, from network security to disaster recovery and infrastructure management. By leveraging managed IT services, businesses can ensure robust cybersecurity, minimize downtime, and enhance operational efficiency. Investing in these services is crucial for maintaining business continuity and protecting valuable digital assets in today’s increasingly complex IT landscape.
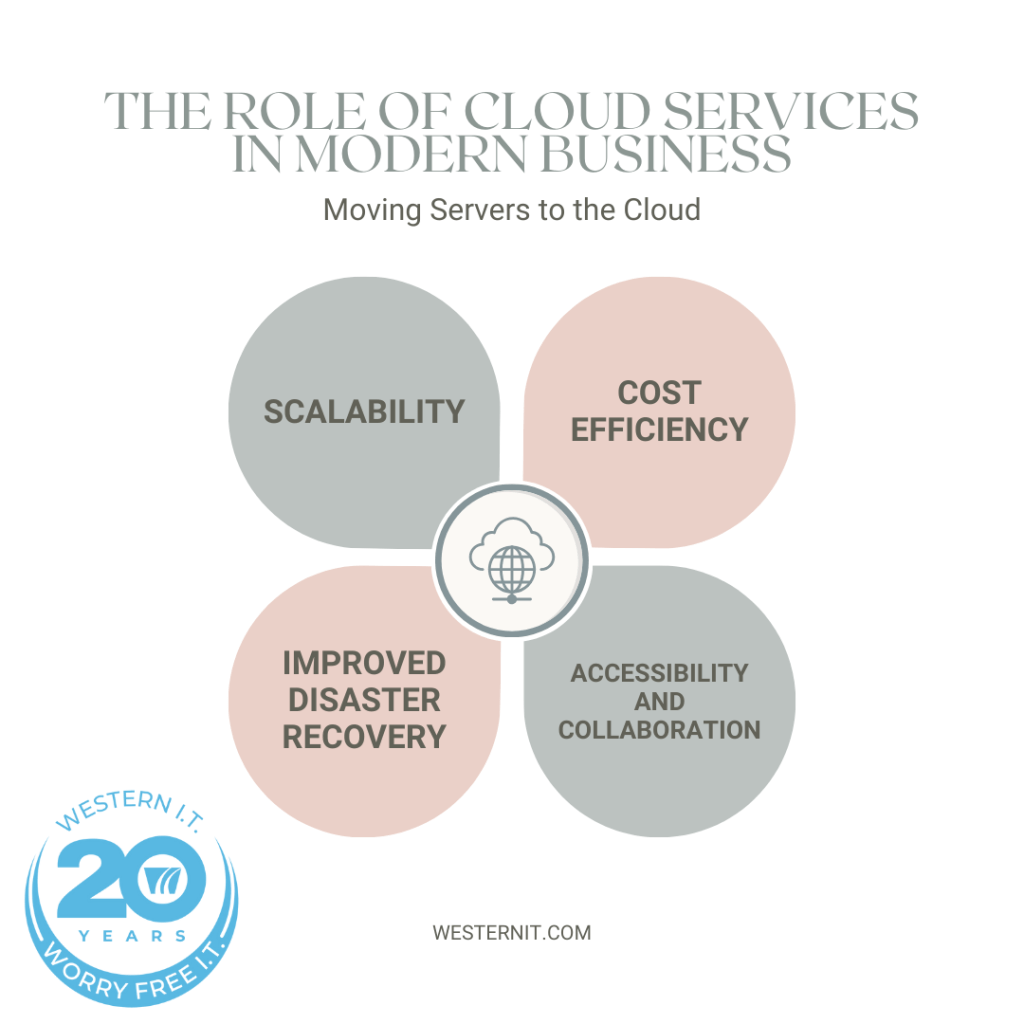
Migrating servers to the cloud has become a strategic move for many modern businesses. This transition offers numerous benefits, including enhanced scalability, cost efficiency, and improved disaster recovery capabilities.
Scalability: One of the most significant advantages of cloud servers is their scalability. Businesses can easily adjust their resources based on current demands without investing in additional hardware. This flexibility ensures that companies can scale up during peak times and scale down during slower periods, optimizing resource utilization and cost.
Cost Efficiency: Cloud migration reduces the need for physical hardware, which can be expensive to purchase and maintain. By moving to the cloud, businesses can convert capital expenditures into operational expenses, paying only for the resources they use. Additionally, cloud service providers often offer competitive pricing and various payment plans, further reducing costs.
Improved Disaster Recovery: Cloud servers provide robust disaster recovery solutions. Data stored in the cloud is often replicated across multiple locations, ensuring that it remains accessible even if one server fails. This redundancy is crucial for maintaining business continuity and minimizing downtime in the event of a disaster.
Accessibility and Collaboration: Cloud servers enable employees to access data and applications from anywhere, promoting remote work and collaboration. This accessibility is particularly beneficial in today’s increasingly mobile work environment, allowing teams to work together seamlessly regardless of their location.
Migrating to Microsoft 365 offers several advantages for businesses, including enhanced productivity, security, and collaboration tools.
Enhanced Productivity: Microsoft 365 provides a suite of productivity tools such as Word, Excel, PowerPoint, and Outlook, all accessible from any device with internet connectivity. This accessibility ensures that employees can work efficiently, whether they are in the office or on the go.
Security: Microsoft 365 includes advanced security features to protect sensitive data. These features include multi-factor authentication, data encryption, and threat detection, ensuring that business information is secure.
Collaboration Tools: Microsoft 365 offers various collaboration tools, such as Teams, SharePoint, and OneDrive. These tools enable real-time collaboration, allowing teams to work together more effectively and share documents seamlessly.
Migration Process: The migration process to Microsoft 365 involves several steps, including planning, data migration, and user training. A detailed migration plan ensures that all data is transferred smoothly with minimal disruption to business operations. User training is crucial to help employees adapt to the new system and utilize its features effectively.
Azure support plays a vital role in managing cloud services and ensuring that businesses can leverage the full potential of Azure’s capabilities.
Comprehensive Management: Azure support provides comprehensive management of cloud services, including virtual machines, databases, and applications. This management ensures that resources are optimized and running efficiently.
Local Azure Services: Local Azure services offer region-specific solutions that cater to the unique needs of businesses in different locations. These services ensure compliance with local regulations and provide lower latency, improving performance.
Expert Guidance: Azure support includes access to a team of experts who can guide best practices, troubleshooting, and optimization. This expertise helps businesses make the most of their Azure investment and address any challenges that arise.
Data replication and SharePoint backup are crucial for ensuring data security and availability.
Data Replication: Data replication involves copying data from one location to another to ensure that a backup is always available. This process protects against data loss due to hardware failures, cyber-attacks, or other disasters. By replicating data to multiple locations, businesses can ensure that their information is always accessible and secure.
SharePoint Backup: SharePoint is a widely used collaboration platform that stores a significant amount of business data. Regular backups of SharePoint ensure that this data is protected and can be restored in case of accidental deletion, corruption, or cyber-attacks. SharePoint backup solutions often include features such as point-in-time restoration and automated backup schedules, enhancing data protection.
Moving from an on-premises Exchange server to the cloud and utilizing Microsoft 365 backup offers several benefits:
Exchange to Cloud Migration: Migrating Exchange to the cloud involves transferring email services from on-premises servers to cloud-based solutions like Microsoft 365. This migration provides enhanced accessibility, allowing users to access their emails from any device with an internet connection. It also reduces the need for physical infrastructure and maintenance, lowering operational costs.
Microsoft 365 Backup: While Microsoft 365 provides robust security features, it’s essential to have a comprehensive backup solution. Microsoft 365 backup ensures that all data, including emails, documents, and SharePoint files, is regularly backed up and can be restored if needed. This backup protects against accidental deletions, data corruption, and cyber threats.
Benefits of Microsoft 365 Backup: Regular backups provide peace of mind, knowing that data can be recovered quickly and efficiently. Microsoft 365 backup solutions often include granular recovery options, allowing businesses to restore specific items or entire accounts as needed. This flexibility ensures that business operations can continue smoothly, even in the event of data loss.
Penetration testing, often referred to as ethical hacking, is a critical component of advanced cybersecurity strategies. It involves simulating cyber attacks on a system, network, or application to identify vulnerabilities that could be exploited by malicious actors. Penetration testing helps organizations understand the weaknesses in their security infrastructure, allowing them to address these vulnerabilities before they can be exploited.
The role of penetration testing in identifying vulnerabilities is multifaceted. Firstly, it provides a realistic assessment of an organization’s security posture by revealing how an attacker could gain unauthorized access to sensitive information. This insight is crucial for developing effective countermeasures and improving overall security.
Moreover, penetration testing helps in evaluating the effectiveness of existing security measures. By challenging the system’s defences, it ensures that the security protocols in place are robust and capable of withstanding real-world attacks. Regular penetration testing is essential for maintaining a high level of security, especially as new vulnerabilities and threats emerge.
In addition to penetration testing, secure server software is fundamental to protecting critical business data and applications. Secure server software includes features such as encryption, access controls, and regular updates to protect against known vulnerabilities. Implementing secure server software ensures that the servers are resistant to attacks and that sensitive data remains protected.
Data encryption is a pivotal aspect of protecting sensitive information in any cybersecurity strategy. It involves converting data into a code to prevent unauthorized access. Only those with the correct decryption key can access the original data, making encryption an effective way to protect information from cyber threats.
The importance of data encryption cannot be overstated. As businesses increasingly rely on digital data, the risk of data breaches grows. Encryption provides a critical layer of security that protects data in transit and at rest. This means that even if data is intercepted or accessed by unauthorized individuals, it remains unreadable and useless without the decryption key.
Data encryption services ensure that sensitive information, such as financial records, customer data, and intellectual property, is protected against theft and tampering. These services often include encryption algorithms, key management, and secure data storage solutions. By implementing robust encryption practices, businesses can comply with regulatory requirements and enhance their overall security posture.
Working with specialized IT providers and consultants offers significant benefits for businesses aiming to enhance their security and operational efficiency. Business IT providers offer a range of services tailored to meet the specific needs of different industries. These services include network management, cybersecurity, cloud solutions, and more.
IT consultancy involves strategic planning and advisory services to help businesses align their IT infrastructure with their goals. IT consultants bring expertise and experience, providing valuable insights into the latest technologies and best practices. They can assess current systems, identify areas for improvement, and develop a roadmap for achieving optimal performance and security.
The benefits of working with specialized IT providers and consultants include access to cutting-edge technology, improved security measures, and cost savings. These professionals can help businesses implement effective security protocols, optimize their IT infrastructure, and ensure compliance with industry standards.
Data recovery services are crucial for businesses that experience data loss due to hardware failures, software issues, or cyber-attacks. RAID recovery and tape backup fixes are specialized services that address these specific challenges.
RAID Recovery: RAID (Redundant Array of Independent Disks) systems are used to store large amounts of data with redundancy to protect against data loss. However, RAID systems can fail due to various reasons, including disk failures, controller issues, or configuration errors. RAID recovery services involve diagnosing and repairing the RAID array to recover lost data. These services require specialized knowledge and tools to rebuild the array and restore the data accurately.
What are Tape Backup Fixes?
Tape Backup Fixes: Tape backups are used for long-term data storage and archiving. They are reliable but can be prone to issues such as tape degradation, read/write errors, and mechanical failures. Tape backup fix services involve repairing and restoring data from damaged or corrupted tapes. These services ensure that critical data is retrievable, even if the physical media is compromised.
Having local support for specific IT products, such as Western IT, provides several advantages for businesses. Western IT offers cloud-managed IT solutions, including wireless, switching, security, and mobile device management. Local support ensures that businesses receive timely assistance and expertise tailored to their specific needs and environment.
Advantages of Local IT Support:
The digital age has revolutionized the way businesses operate, offering unprecedented opportunities for growth, innovation, and connectivity. However, this transformation has also introduced a complex and ever-evolving landscape of cyber threats. Cybercriminals are becoming increasingly sophisticated, employing advanced techniques to exploit vulnerabilities and gain unauthorized access to sensitive information. From ransomware attacks that hold critical data hostage to intricate phishing schemes that deceive even the most vigilant users, the threat landscape is continuously changing.
The rise of Internet of Things (IoT) devices, cloud computing, and remote work environments has expanded the attack surface, providing cybercriminals with more entry points to exploit. As these technologies continue to integrate into business operations, the potential for security breaches grows exponentially. Additionally, state-sponsored cyber attacks and organized cybercrime groups pose significant challenges, targeting not only private enterprises but also critical infrastructure and government systems.
Given this dynamic environment, businesses must recognize that cybersecurity is not a one-time investment but an ongoing process. Staying ahead of cyber threats requires continuous monitoring, regular updates, and proactive measures to identify and mitigate risks before they can cause harm. The ability to adapt to new threats swiftly and effectively is crucial for maintaining the integrity and security of business operations.
In the face of these evolving threats, proactive IT management has never been more critical. Proactive IT management involves anticipating potential issues and implementing measures to prevent them rather than merely reacting to problems as they arise. This approach ensures that businesses are not only prepared to respond to cyber incidents but also equipped to prevent them from occurring in the first place.
Effective IT management encompasses several key practices, including regular security assessments, timely software updates, and comprehensive employee training programs. By conducting regular security assessments, businesses can identify vulnerabilities in their systems and address them promptly. Keeping software up-to-date is essential for protecting against known threats, as outdated software can be a significant security risk.
Employee training is another vital component of proactive IT management. Human error is a leading cause of security breaches, often through phishing attacks or accidental data leaks. By educating employees on best practices for cybersecurity, businesses can significantly reduce the risk of successful attacks. Training should cover topics such as recognizing phishing emails, using strong passwords, and following secure data handling procedures.
Moreover, a proactive IT strategy includes implementing advanced cybersecurity solutions such as firewalls, intrusion detection systems, and data encryption. These technologies provide multiple layers of defence, making it more difficult for cybercriminals to penetrate systems and access sensitive information. Additionally, regular backup and disaster recovery planning ensures that businesses can quickly recover from any incidents that do occur, minimizing downtime and data loss.
In today’s rapidly changing digital landscape, businesses cannot afford to be complacent about cybersecurity. The stakes are too high, with potential consequences ranging from financial losses and reputational damage to legal liabilities and operational disruptions. To safeguard their operations and ensure long-term success, businesses must invest in comprehensive IT support, managed IT services, and robust cybersecurity measures.
Western IT Company is uniquely positioned to help businesses navigate the complexities of modern cybersecurity. With a team of experienced professionals and a wide range of services, Western IT provides the expertise and support needed to protect against evolving cyber threats. Our managed IT services include network security, data encryption, secure server management, and more, ensuring that your IT infrastructure is resilient and secure.
We understand that every business is different, which is why we offer tailored solutions to meet your specific needs. Whether you require advanced penetration testing to identify vulnerabilities, data recovery services to protect against data loss or local support for specialized IT products like Meraki, Western IT has you covered. Our proactive approach to IT management ensures that potential issues are addressed before they can impact your business, providing peace of mind and allowing you to focus on what you do best.
In conclusion, the future of cybersecurity and IT services lies in the ability to anticipate and adapt to new threats continuously. By partnering with Western IT Company, you can leverage our comprehensive suite of services and expertise to stay ahead of the curve. Don’t wait for a cyber attack to happen—act now to protect your business. Invest in robust cybersecurity measures, proactive IT management, and expert support from Western IT to secure your operations and ensure long-term success. Contact us today to learn more about how we can help you build a resilient and secure IT environment. Your business’s future depends on it.
Worried about being a target for phishing attacks? Protect your company today!
Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity....
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit...