Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...


Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit card...
This in-depth cybersecurity planning guide provides information and advice to help organizations develop a successful strategy...

While home health agencies face distinct health IT challenges, collaboration and innovation are crucial for overcoming these...

The umbrella term malware is one of the greatest cybersecurity threats enterprises face. Learn about 12 common types of malware...

Matching with Western I.T.: Our services extend beyond strategy development. With solutions like Malware & Intrusion Detection and Cloud Data Backups, we ensure that your cybersecurity strategy remains effective and up-to-date, allowing you to respond promptly to new challenges.
Cybersecurity Strategy Guide. In today’s ever-evolving digital landscape, ensuring the security of your organization’s assets is not just a necessity, but a strategic imperative. Crafting an effective cybersecurity strategy is the cornerstone of this effort. This guide presents a step-by-step approach to building a robust cybersecurity strategy that not only shields your business but also sets the stage for growth and success.
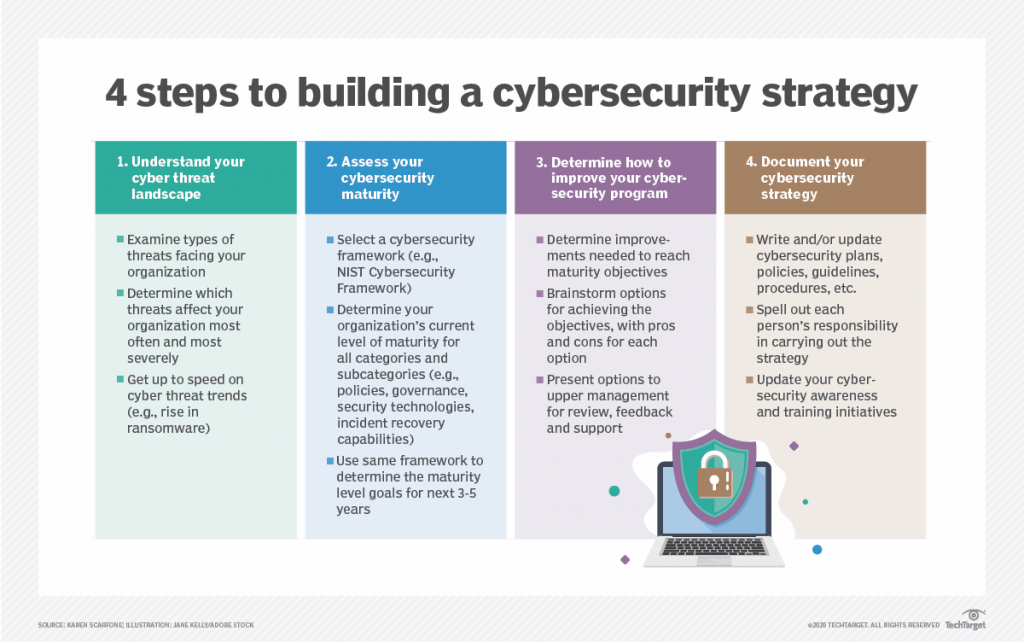
The first stride towards a fortified cybersecurity strategy is understanding your organization’s cyber threat landscape. Delve into the types of attacks your business frequently encounters, be it malware, phishing, or insider threats. Scrutinize competitors’ experiences with major incidents to identify patterns. This insight empowers you to anticipate and proactively combat potential threats.
Assessing your organization’s cybersecurity maturity is crucial for effective strategy development. Utilize established frameworks like the NIST Cybersecurity Framework to evaluate your current state and set targets for growth. Pinpoint areas requiring enhancement, be it technology, policies, or incident response capabilities. This evaluation lays the groundwork for your strategic objectives.
Leverage your assessment to formulate a roadmap for bolstering your cybersecurity program. Identify requisite tools and capabilities to achieve your objectives. Evaluate options for implementation, considering resource allocation and potential outsourcing. Garner support from upper management to ensure alignment and successful execution.
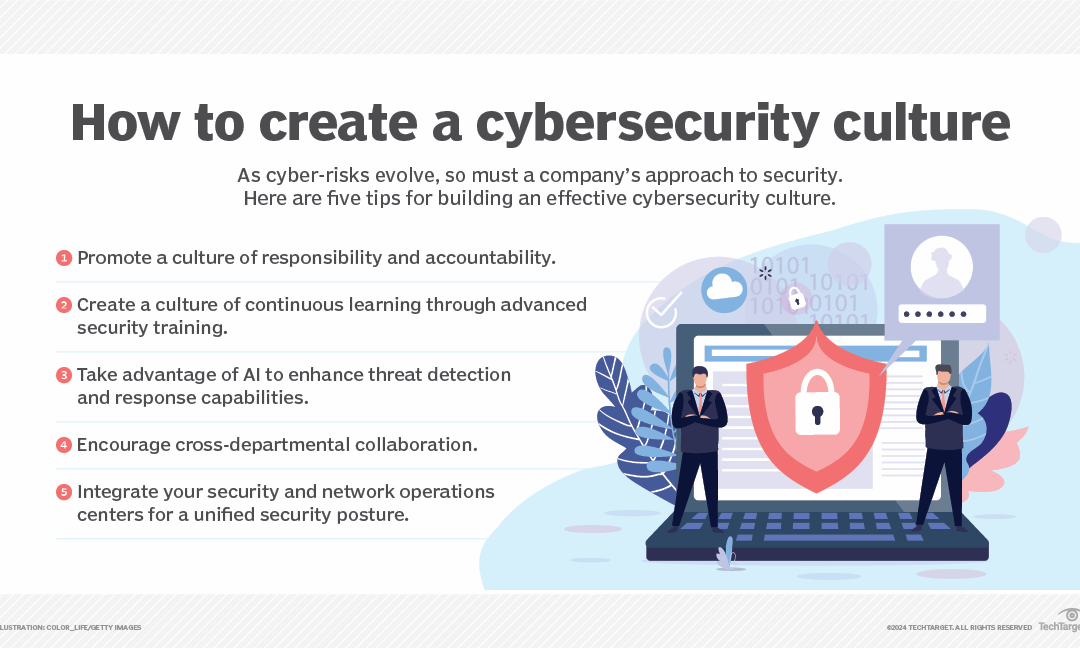
A robust cybersecurity strategy hinges on comprehensive documentation. Detail risk assessments, plans, policies, guidelines, and procedures. Define roles and responsibilities with clarity to ensure accountability. Foster a culture of awareness within your team through transparent communication. Additionally, regularly update training programs to maintain a vigilant workforce.
At this juncture, consider Western I.T. as your trusted partner in cybersecurity excellence. Our suite of services perfectly aligns with the steps outlined above, providing you with tailored solutions for a fortified digital defense.
From our WITProtect package, encompassing a multi-layered defense system against diverse cyber threats, to our advanced Malware & Intrusion Detection solution, ensuring proactive identification and mitigation of potential breaches – Western I.T. stands as your steadfast ally in securing your digital realm.
Furthermore, our Cloud Data Backups service ensures the safety and recoverability of your critical data, enabling seamless business continuity even in the face of unexpected challenges. With our expertise and your commitment, a resilient cybersecurity strategy is within reach.
A robust cybersecurity strategy is not static; it’s a dynamic endeavor that requires vigilance and adaptability. By adhering to these steps and partnering with Western I.T., you’re not just safeguarding your organization – you’re fortifying it for an ever-evolving digital future.
Worried about being a target for phishing attacks? Protect your company today!
Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity....
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit...