Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...


Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit card...
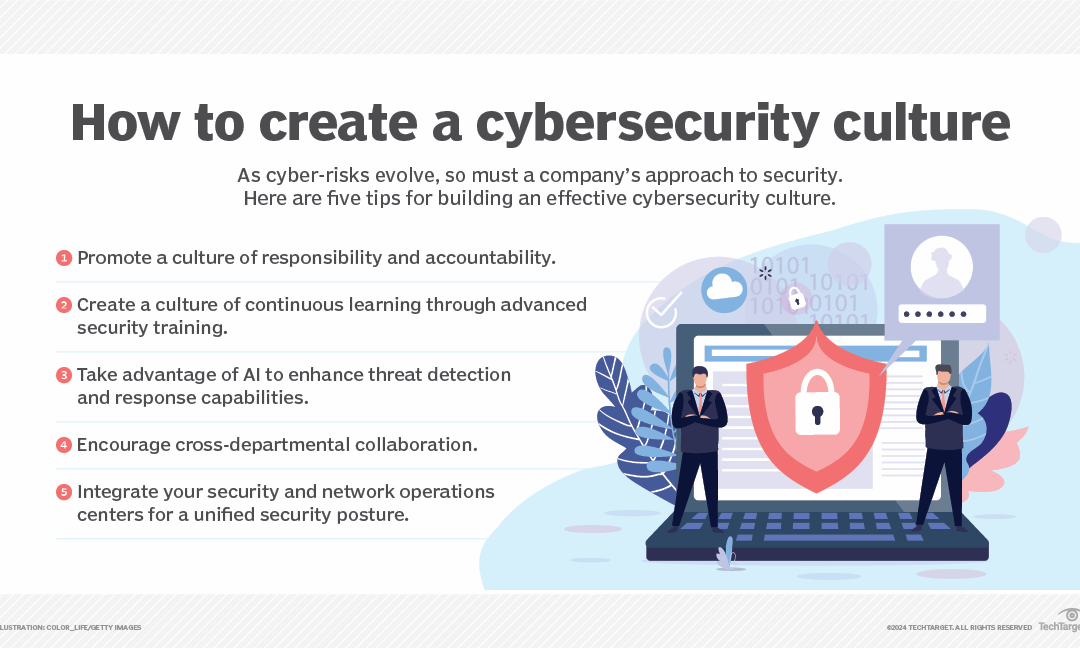
This in-depth cybersecurity planning guide provides information and advice to help organizations develop a successful strategy...

While home health agencies face distinct health IT challenges, collaboration and innovation are crucial for overcoming these...

The umbrella term malware is one of the greatest cybersecurity threats enterprises face. Learn about 12 common types of malware...
Cybersecurity is a cornerstone of business integrity. At Western I.T., we prioritize your digital safety. Let’s explore key strategies for protecting your working PCs from cyberattacks.
Cyber threats range from malware to sophisticated phishing attacks. Recognizing these threats is the first step in robust cyber defence.
Cybersecurity is a dynamic, ongoing process. By integrating these practices, you significantly enhance your Cybersecurity against cyber threats. Remember, proactive measures and continuous education are your best tools in the fight against cybercrime.
Worried about being a target for phishing attacks? Protect your company today!
Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity....
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit...