Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...


Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit card...
This in-depth cybersecurity planning guide provides information and advice to help organizations develop a successful strategy...

While home health agencies face distinct health IT challenges, collaboration and innovation are crucial for overcoming these...

Understanding Managed IT Services What Are Managed IT Services? Managed IT Services For business are the comprehensive...
Cyberattacks are on the Rise: Is Your Business Prepared
Cybersecurity Essentials has become a cornerstone of managed IT services. With businesses increasingly relying on technology for their operations, the risks associated with cyber threats have escalated. Managed IT service providers play a crucial role in safeguarding business data and ensuring seamless operations by implementing robust cybersecurity measures. This article delves into common cyber threats, Cybersecurity Essentials preventive measures, and the importance of a comprehensive cybersecurity strategy to protect your business.
Cyber threats are evolving, becoming more sophisticated and damaging. Here are some of the most common threats businesses face today:

Cybersecurity Essentials: To combat these threats, managed IT service providers implement a range of preventive measures designed to protect business data and ensure system integrity.
Human error remains one of the most significant risks to cybersecurity. Employees are often the first line of defence against cyber threats, making training an essential component of a comprehensive cybersecurity strategy.
Despite best efforts, breaches can still occur. Having a robust disaster recovery plan in place ensures that your business can quickly recover and minimize the impact of a cybersecurity incident.
Several businesses have successfully implemented robust cybersecurity measures, demonstrating the effectiveness of comprehensive cybersecurity strategies.
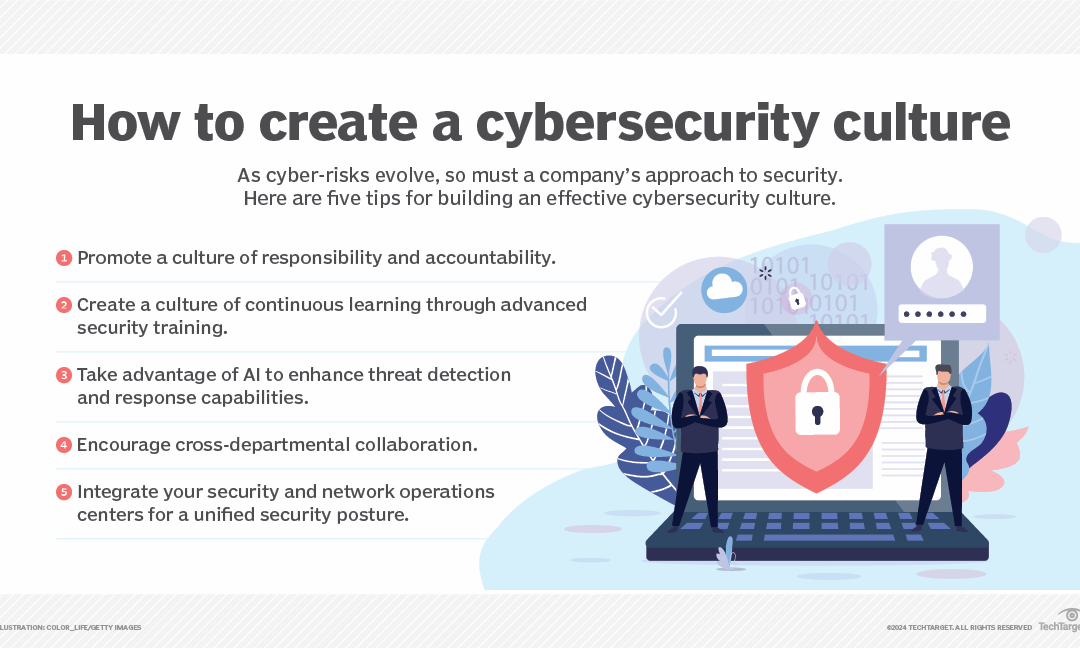
In the ever-evolving landscape of cyber threats, businesses must adopt a proactive and comprehensive approach to cybersecurity. Managed IT service providers play a critical role in implementing and maintaining these defences. Regular security assessments, advanced endpoint protection, employee training, and disaster recovery planning are essential components of a robust cybersecurity strategy. By partnering with a managed IT service provider, businesses can ensure they are well-protected against the myriad of cyber threats that could compromise their operations and data integrity.
Protect your business with Western I.T.’s comprehensive managed IT and cybersecurity services. Contact us today to schedule a free consultation and learn how we can help safeguard your business against cyber threats. Visit our new office in Detroit or reach out online to start your journey toward a more secure future.
Cybersecurity Essentials. In a digital era brimming with cyber threats, ensuring the security of your business is paramount. Western I.T. introduces WIT Protect, a comprehensive cybersecurity package that stands as a stalwart shield against the ever-evolving landscape of viruses and malware.
Cybersecurity refers to the practice of protecting systems, networks, and data from digital attacks. It involves implementing measures to guard against unauthorized access, data breaches, and cyber threats like malware, ransomware, and phishing. Cybersecurity Essentials. Effective cybersecurity ensures the integrity, confidentiality, and availability of information, safeguarding businesses and individuals from financial loss, reputational damage, and operational disruptions. With the increasing reliance on digital technology, robust cybersecurity practices are essential for maintaining a secure digital environment.
Worried about being a target for phishing attacks? Protect your company today!
Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity....
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit...