Why Your Business Needs Cybersecurity More Than Ever? In today's hyper-connected digital world, cybersecurity is no longer a...


Why Your Business Needs Cybersecurity More Than Ever? In today's hyper-connected digital world, cybersecurity is no longer a...

Worried about being a target for phishing attacks? Protect your company today!

Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit card...
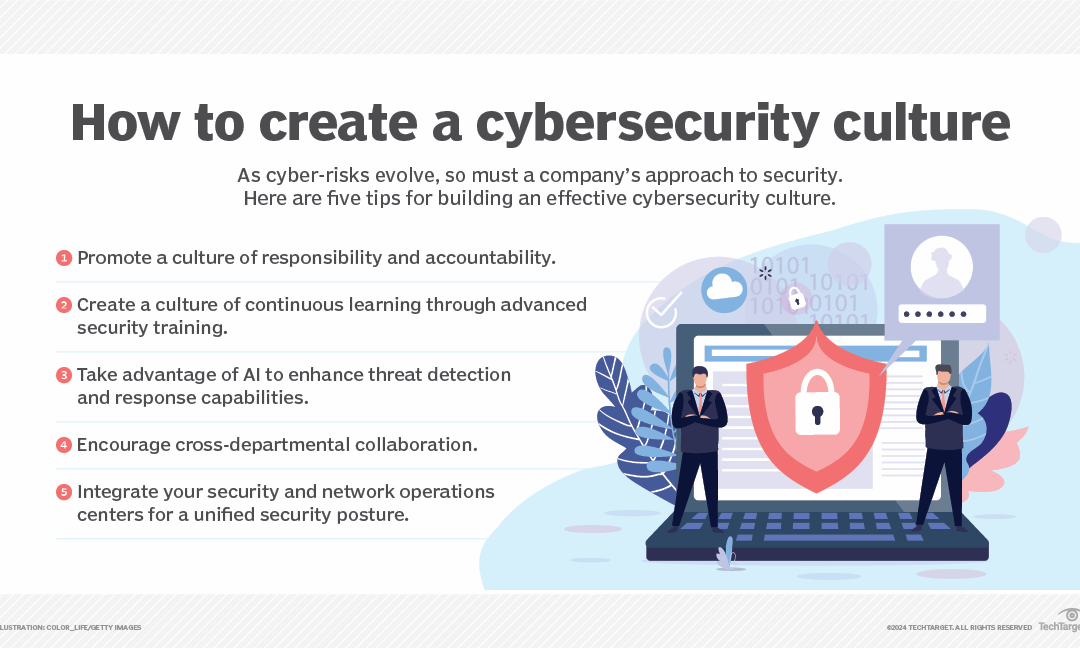
This in-depth cybersecurity planning guide provides information and advice to help organizations develop a successful strategy...
In an era where data breaches and cyber threats are on the rise, cyber security for business is not just an option; it’s a necessity. Protecting your sensitive information from malicious attacks is crucial for maintaining your business’s integrity and trustworthiness. Effective cyber security measures can safeguard your business operations, protect customer data, and ensure compliance with industry regulations.

Advanced Tools and Techniques
To protect your business effectively, you must utilize advanced tools and techniques for threat detection. These tools help identify potential threats before they escalate into serious issues. Implementing a robust threat detection system allows your organization to monitor network activity in real time, identify suspicious behaviour, and respond swiftly to mitigate risks.
Proactive Monitoring
Proactive monitoring involves continuously analyzing network traffic, system logs, and user behaviour to detect anomalies that may indicate a cyber attack. Tools like Intrusion Detection Systems (IDS) and Security Information and Event Management (SIEM) solutions are critical in this process. These systems provide real-time alerts and comprehensive reports, enabling your IT team to address threats promptly.
Machine Learning and AI
Incorporating machine learning and artificial intelligence into your cyber security strategy can significantly enhance threat detection capabilities. These technologies can analyze vast amounts of data to identify patterns and predict potential threats. By leveraging AI, businesses can stay ahead of cyber criminals and protect their assets more effectively.
Encryption
One of the most effective ways to protect your business data is through encryption. Encryption converts sensitive information into unreadable code that can only be deciphered with the appropriate decryption key. This ensures that even if data is intercepted, it remains inaccessible to unauthorized users.
Access Control
Implementing strict access control measures is crucial for data protection. This involves defining who can access specific information within your organization and ensuring that access is granted based on the principle of least privilege. Multi-factor authentication (MFA) adds a layer of security by requiring users to provide multiple forms of identification before accessing sensitive data.
Regular Backups
Regularly backing up your data is essential for protecting against data loss due to cyber attacks or system failures. Backups should be stored securely, preferably offsite or in the cloud, to ensure data can be recovered in the event of a breach. Regularly test your backup and recovery processes to ensure they work as intended.
Adhering to Industry Regulations
Compliance with industry regulations and standards is a fundamental aspect of cyber security. Regulations such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the Payment Card Industry Data Security Standard (PCI DSS) set guidelines for protecting sensitive information. Non-compliance can result in significant fines and damage to your business’s reputation.
Regular Audits and Assessments
Conducting regular security audits and assessments helps ensure your business complies with relevant regulations. These audits involve reviewing your security policies, procedures, and controls to identify gaps and areas for improvement. Engaging third-party auditors can provide an objective assessment of your security posture and help you address any compliance issues.
Training and Awareness
Educating your employees about compliance requirements and cyber security best practices is crucial. Regular training sessions and awareness programs can help employees recognize and respond to potential threats, reducing the risk of human error leading to a security breach.
When it comes to managing your business’s IT needs, selecting the right service provider is critical. Western IT offers comprehensive managed IT services designed to enhance your cyber security posture, optimize IT operations, and ensure reliable support. Here’s why choosing Western IT is a smart decision:
1. Comprehensive Service Offerings
Western IT provides a wide range of services, including cyber security, cloud solutions, IT support, and custom software development. Their extensive service portfolio ensures that all your IT needs are met under one roof, simplifying management and coordination.
2. Expertise and Experience
With years of experience in the IT industry, Western IT’s team of professionals brings deep expertise to the table. Their knowledge spans various domains, enabling them to tackle complex IT challenges effectively and provide valuable insights to enhance your business’s IT infrastructure.
3. Focus on Cyber Security
Cyber security is a core focus at Western IT. They offer proactive solutions to safeguard your business against evolving cyber threats. From advanced threat detection to comprehensive data protection measures, Western IT ensures your business’s critical assets are secure.
4. Scalability and Flexibility
Western IT’s services are scalable to meet the needs of businesses of all sizes. Whether you’re a small startup or a large enterprise, their solutions can be tailored to fit your specific requirements. This flexibility ensures that as your business grows, your IT infrastructure can scale with it.
5. Customer-Centric Approach
Western IT is committed to delivering exceptional customer service. They prioritize understanding your business’s unique needs and providing personalized solutions. Their proactive approach ensures prompt issue resolution and ongoing support, fostering a strong partnership.
6. Cost-Effective Solutions
By outsourcing your IT needs to Western IT, you can achieve significant cost savings. Their managed services model reduces the need for in-house IT staff and minimizes the costs associated with maintaining IT infrastructure. This allows you to allocate resources more efficiently and invest in other critical areas of your business.
7. Innovative Solutions
Western IT stays at the forefront of technological advancements, offering innovative solutions that drive business growth. Whether it’s adopting the latest cyber security technologies or leveraging cloud computing for enhanced agility, Western IT ensures your business remains competitive.
In conclusion, cyber security is a vital component of any business’s IT strategy. By focusing on threat detection, data protection, and compliance, businesses can safeguard their operations and build trust with customers. Partnering with a trusted service provider like Western IT can enhance your cyber security posture, streamline IT management, and support your business’s growth and success.
Stay Safer, One Email at a Time: Introducing Our New AI-Powered Email Scanner In today's rapidly evolving digital...
Why Your Business Needs Cybersecurity More Than Ever? In today's hyper-connected digital world, cybersecurity is no...
Worried about being a target for phishing attacks? Protect your company today!