Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...


Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity. However, this...
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit card...
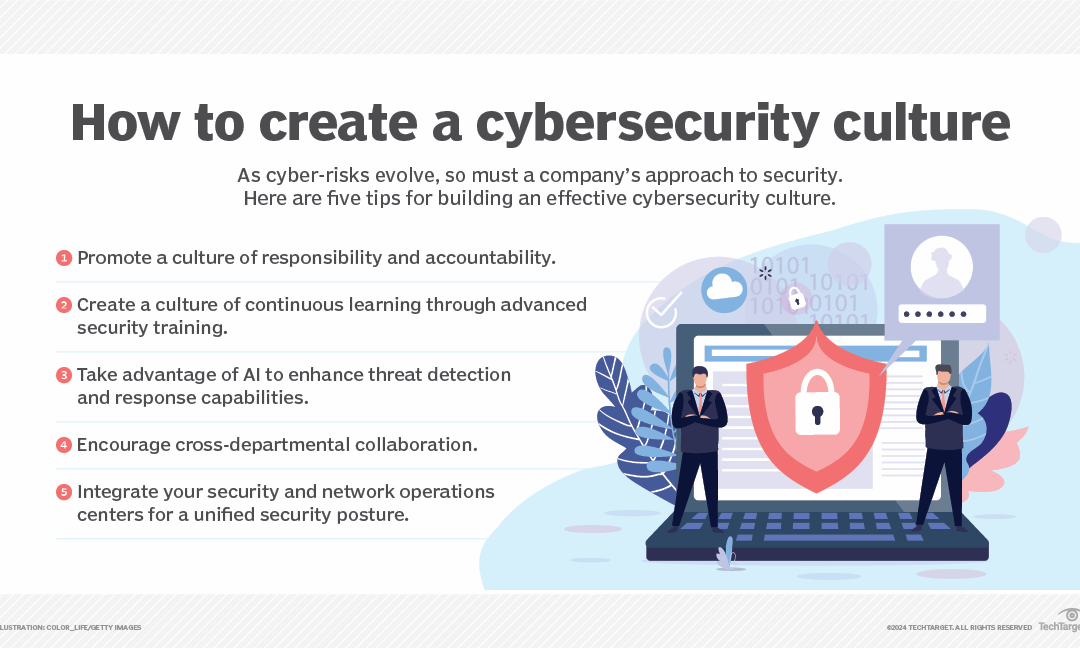
This in-depth cybersecurity planning guide provides information and advice to help organizations develop a successful strategy...

While home health agencies face distinct health IT challenges, collaboration and innovation are crucial for overcoming these...

The umbrella term malware is one of the greatest cybersecurity threats enterprises face. Learn about 12 common types of malware...

Against Cyber Threats. In today’s fast-paced digital landscape, businesses rely heavily on technology to streamline operations, connect with customers, and drive growth. However, with the increasing reliance on technology comes the pressing need to ensure the security of sensitive data and digital assets. Cybersecurity threats and fraud are ever-evolving, making it crucial for businesses to partner with experts who can provide robust solutions. Western I.T. stands as a reliable ally in the realm of cybersecurity, offering comprehensive services that safeguard your business from threats and fraud, ensuring smooth operations and maintaining customer trust.
The modern business ecosystem thrives on interconnectedness, cloud computing, and digital transactions. While these advancements offer unparalleled opportunities, they also open doors for cybercriminals. Cyber threats, ranging from viruses and malware to sophisticated phishing schemes, are on the rise. These threats can compromise sensitive data, disrupt operations, tarnish reputation, and result in significant financial losses. As businesses embrace digital transformation, they must prioritize cybersecurity to ensure not only their own survival but also the trust of their customers and partners.
Western I.T. recognizes the gravity of the cybersecurity challenge and presents an arsenal of solutions to fortify your business’s digital resilience. One such solution is WITProtect, a comprehensive cybersecurity package designed to address the multifaceted nature of cyber threats. At its core, WITProtect offers cutting-edge anti-virus and malware protection. This multi-layered defense system shields your systems, networks, and data from malicious software, preventing unauthorized access and potential damage. With cyber threats becoming increasingly sophisticated, WITProtect ensures that your business is equipped with the latest tools to counteract them.
WITProtect is not just about defense; it extends to recovery and business continuity. In the digital realm, data loss and system disruptions can be devastating. That’s why WITProtect includes a comprehensive backup and recovery strategy. Regular system backups are essential to ensure that your data is secured and can be swiftly restored in case of any unforeseen event. Whether it’s a hardware failure, a cyberattack, or a natural disaster, WITProtect ensures that your business can bounce back with minimal disruptions. This approach not only safeguards your data but also supports the seamless operation of your business, even in the face of adversity.
Every business is unique, and so are its cybersecurity needs. Western I.T. doesn’t offer a one-size-fits-all solution; rather, they work closely with businesses to tailor their cybersecurity strategy. This customized approach takes into account your business’s operations, data dependencies, and recovery time objectives. It ensures that the cybersecurity solution seamlessly integrates into your existing infrastructure, aligning with your business goals and enhancing overall efficiency.
In today’s interconnected world, cybersecurity isn’t an option; it’s a necessity. Cyber threats and fraud are not stagnant; they continually evolve to exploit vulnerabilities. By partnering with Western I.T. and implementing solutions like WITProtect, you elevate your business’s security posture. You not only protect your data and systems but also fortify your brand reputation and customer trust. With the assurance of WITProtect, you can confidently navigate the digital landscape, focus on growth, and drive innovation without the constant fear of cyber threats hindering your progress.
The future of business is digital, and with it comes the imperative of ensuring robust cybersecurity measures. Western I.T. emerges as a guardian of your business’s digital future, offering a suite of solutions that span from defense against cyber threats to data recovery in the aftermath of a disaster. WITProtect isn’t just a package; it’s a promise of protection, resilience, and uninterrupted growth. As you embrace technological advancements, let Western I.T. be your partner in safeguarding your business’s digital journey, ensuring that you’re always one step ahead of the ever-evolving landscape of cybersecurity threats and fraud.
A strategic plan to restore data and operations after disaster, ensuring continuity and minimizing downtime.
It’s Western I.T.’s proactive solution to identify and counteract malware and network intrusion threats.
WITProtect is a comprehensive cybersecurity package by Western I.T., including anti-virus protection and system recovery solutions.
Worried about being a target for phishing attacks? Protect your company today!
Understand the Holiday Season Cyber Threats The holiday season is a time for joy, celebration, and generosity....
Cybercriminals steal credit card? Cybercriminals have various methods at their disposal to hack and exploit credit...